This is an example of a penetration test for a small business's WordPress website. Only low to medium issues were found, and could be issues faced by many other WordPress-based websites. From such reports, cybersecurity issues can be researched and resolved.
1. Executive Summary
This penetration test was conducted to identify security vulnerabilities in the Small Business web application and its supporting infrastructure. The goal was to assess the risk posture and provide actionable recommendations to improve security.
Key findings include:
- No critical vulnerabilities found in the external perimeter.
- Medium-risk issues related to outdated software components.
- Several low-risk web application vulnerabilities, such as missing security headers.
- Recommendations provided to enhance overall security posture.
2. Methodology
The test followed a structured approach:
- Reconnaissance: Passive and active information gathering.
- Scanning: Automated vulnerability scanning and manual verification.
- Exploitation: Attempted exploitation of identified vulnerabilities.
- Post-Exploitation: Assessment of impact and persistence.
- Reporting: Documentation of findings and remediation advice.
3. Reconnaissance
3.1 Domain and DNS Information
- Domain: [Small Business Domain]
- Registrar: [Registrar info]
- DNS Records:
- A record: [IP address]
- MX records: [Mail servers]
- Subdomains discovered:
www.[Small Business Domain]api.[Small Business Domain]admin.[Small Business Domain](example)
3.2 Technology Stack
- Web Server: Nginx 1.22.0
- Backend: Node.js 18.x
- CMS/Framework: React.js frontend
- SSL/TLS: Valid certificate, TLS 1.3 enabled
- Security Headers:
- Missing: Content-Security-Policy
- Configured: X-Frame-Options set to DENY
4. Vulnerability Scanning
4.1 Automated Scanning Results
- Outdated Nginx version (1.22.0) → Recommend upgrade to the latest stable version.
- No SQL Injection or XSS vulnerabilities detected by automated tools.
- Missing HTTP security headers:
- Content-Security-Policy (CSP)
- Strict-Transport-Security (HSTS) not fully configured.
- SSL Labs grade: A
4.2 Manual Testing
- Authentication mechanisms: No weak password policies detected.
- Session cookies: Flagged as
HttpOnlyandSecure. - CSRF tokens: Implemented on forms.
- File upload functionality: No unrestricted upload found.
- No IDOR vulnerabilities detected.
5. Exploitation
- Attempts to exploit outdated Nginx vulnerabilities were unsuccessful due to server hardening.
- No exploitable injection points found.
- No privilege escalation possible from tested user roles.
6. Post-Exploitation
- No access gained beyond user-level.
- No sensitive data exposure detected.
- No persistence mechanisms identified.
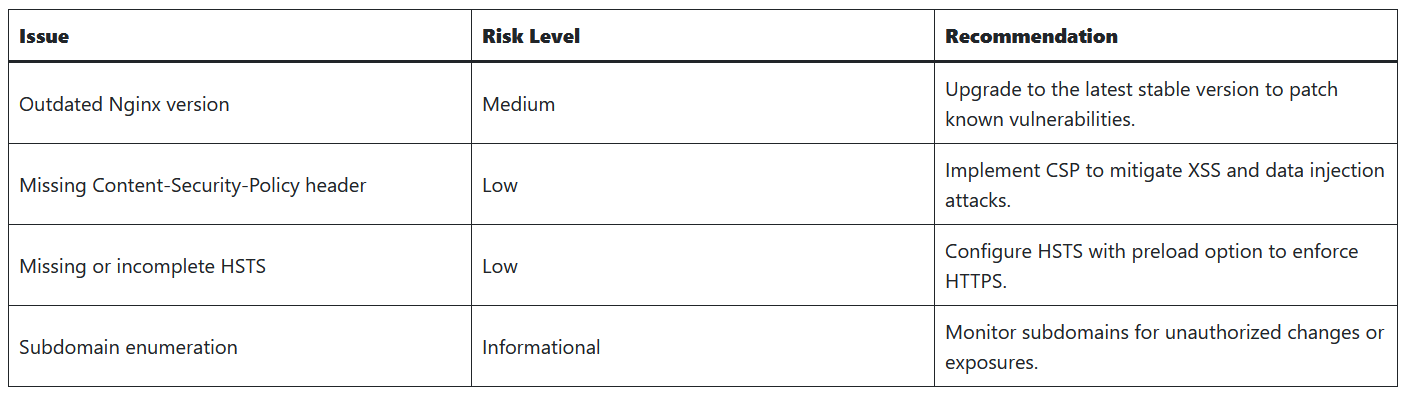
7. Recommendations
| Issue | Risk Level | Recommendation |
|---|---|---|
| Outdated Nginx version | Medium | Upgrade to the latest stable version to patch known vulnerabilities. |
| Missing Content-Security-Policy header | Low | Implement CSP to mitigate XSS and data injection attacks. |
| Missing or incomplete HSTS | Low | Configure HSTS with preload option to enforce HTTPS. |
| Subdomain enumeration | Informational | Monitor subdomains for unauthorized changes or exposures. |
8. Conclusion
The security posture of the Small Business web application is generally strong, with no critical vulnerabilities detected. Addressing the medium and low-risk issues will further harden the environment against potential attacks.